In a significant cybersecurity operation, Microsoft, in collaboration with global law enforcement agencies, successfully disrupted the Lumma Stealer malware network. This malware had infected over 394,000 Windows computers worldwide between March 16 and May 16, 2025, stealing sensitive data such as passwords, credit card information, and cryptocurrency wallet credentials.
Table of contents
What is Lumma Stealer?
Lumma Stealer, also known as LummaC2, is a type of information-stealing malware that emerged in 2022. It works through a Malware-as-a-Service (MaaS) system, where hackers can pay a monthly fee between $250 and $1,000 to use it. The malware targets Windows operating systems, extracting data from web browsers and applications, including passwords, cookies, credit card details, and cryptocurrency wallet information.
15 Proven Ways to Make Money Using Your Mobile Phone in 2025
How Does Lumma Stealer Work?
Lumma Stealer employs sophisticated techniques to evade detection and analysis:
- Anti-Analysis Measures : It uses trigonometry to analyze mouse movements, determining if it’s running on a real machine or in a sandbox environment. If the movements don’t mimic human behavior, the malware halts its operations.
- Encrypted Communication : The malware communicates with its command-and-control (C2) servers using encrypted channels, making it difficult for security tools to intercept and analyze the data.
- Data Exfiltration : Once active, Lumma Stealer collects data from browsers, email clients, FTP clients, and cryptocurrency wallets, sending the information to its C2 servers.
Distribution Methods
Hackers use different ways to spread Lumma Stealer
How to Remove Personal Information from the Internet (2025)
- Phishing Emails : Emails containing malicious attachments or links impersonating reputable organizations.
- Malicious Advertisements : Fake ads leading to websites that prompt users to download and execute the malware.
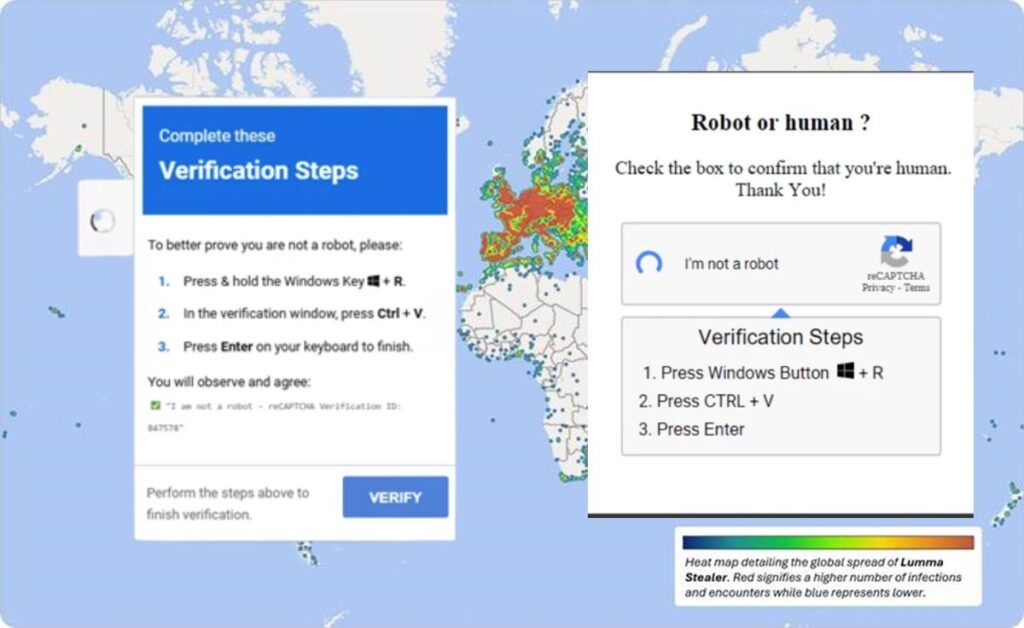
- Social Engineering : Hackers use fake CAPTCHA checks and fake invoices to fool people into running harmful codes.
The Takedown Operation
Microsoft’s Digital Crimes Team, helped by the U.S. government, Department of Justice, Europol, Japan’s Cybercrime Control Center, and companies like Cloudflare, executed the takedown by seizing over 2,300 domains and dismantling Lumma’s command-and-control infrastructure.
Switch from Skype to Microsoft Teams | Free And Easy Guide
They redirected over 1,300 of these domains to secure Microsoft-controlled servers, effectively severing communications between the malware and its operators.
Ongoing Threat
Despite this significant disruption, experts warn that the threat from information stealers like Lumma remains high. Their effectiveness and broad adoption make them indispensable tools for cybercriminals and even nation-state actors.
How to Backup Android Contacts to OneDrive (2025)
Protecting Yourself
To safeguard against threats like Lumma Stealer:
- Stay Updated : Ensure your operating system and all software are up to date with the latest security patches.
- Install Antivirus Program : Get a trusted antivirus app and make sure it stays updated regularly.
- Be Careful with Emails : Don’t open files or click links in emails from people you don’t know or messages that seem strange.
- Verify Downloads : Only download software from official and trusted websites.
By following these practices, individuals and organizations can reduce the risk of falling victim to malware like Lumma Stealer.